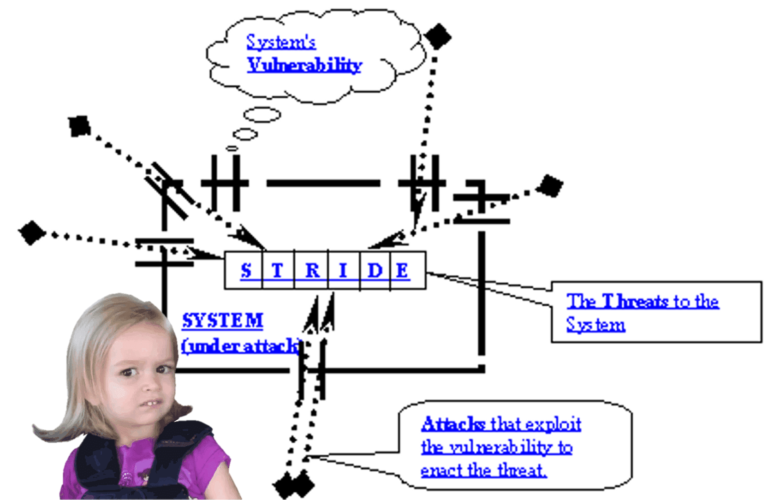
In 1999, the Microsoft Security Task Force introduced the STRIDE “threat” model as a means of identifying threats to Microsoft products during the design phase. STRIDE is an acronym that represents six “threat” categories. According to the paper that introduced the STRIDE model, “The Threats to our Products”, the intent of these six threat categories […]

Professional & Discrete Cybersecurity Services
Cyber threat actors perpetually impose risk and cost to businesses and critical infrastructure worldwide. From insider threats to nation-state actors, Enclave Defense is committed to providing services that help our clients understand and mitigate the cyber risk they represent.

Services
Risk Assessments
We provide a holistic review of the cyber threats most relevant to our clients, the vulnerabilities those threat may exploit, and the resulting impact on operations. We can provide this assessment in accordance with IEC 62443, NIST, or other standards relevant to our client’s industry or sector.
Red Teaming
While expertly avoiding disruptions to critical operations, we will identify and report on human and technical weaknesses before an actual malicious threat does.
Project Management
Whether our clients are seeking to develop, test, or acquire new cybersecurity capabilities or bolster operational security (OPSEC) against prying threat actors, we ensure they achieve their programs objectives and milestones.

YouTube / Podcast
“Cyber moves pretty fast. If you don’t stop and look around once in a while, you could miss it.”
Cyber Myler
Stay fresh on InfoSec happenings by checking out our blog and the Enclave Defense-sponsored “Cyber Myler’s” podcast / YouTube videos.
Blog
Ransomware Targeting of ICS Sectors Highlights Risk Assessment Nuance (ft. Dragos + Conti)
For ransomware attackers, as with all malicious cyber threat actors, a target's vulnerabilities are a critical means, not the end.
TSA’s Security Directive on Enhancing Passenger Rail Cybersecurity Doesn’t Apply to Your Transit Agency — But Should it?
The validity of TSA's determination of "higher risk" passenger rail systems is only as strong as the apparent assumption that a given threat is targeting small and large systems alike to disrupt the entirety of one of the eight urban areas selected.
Our Team