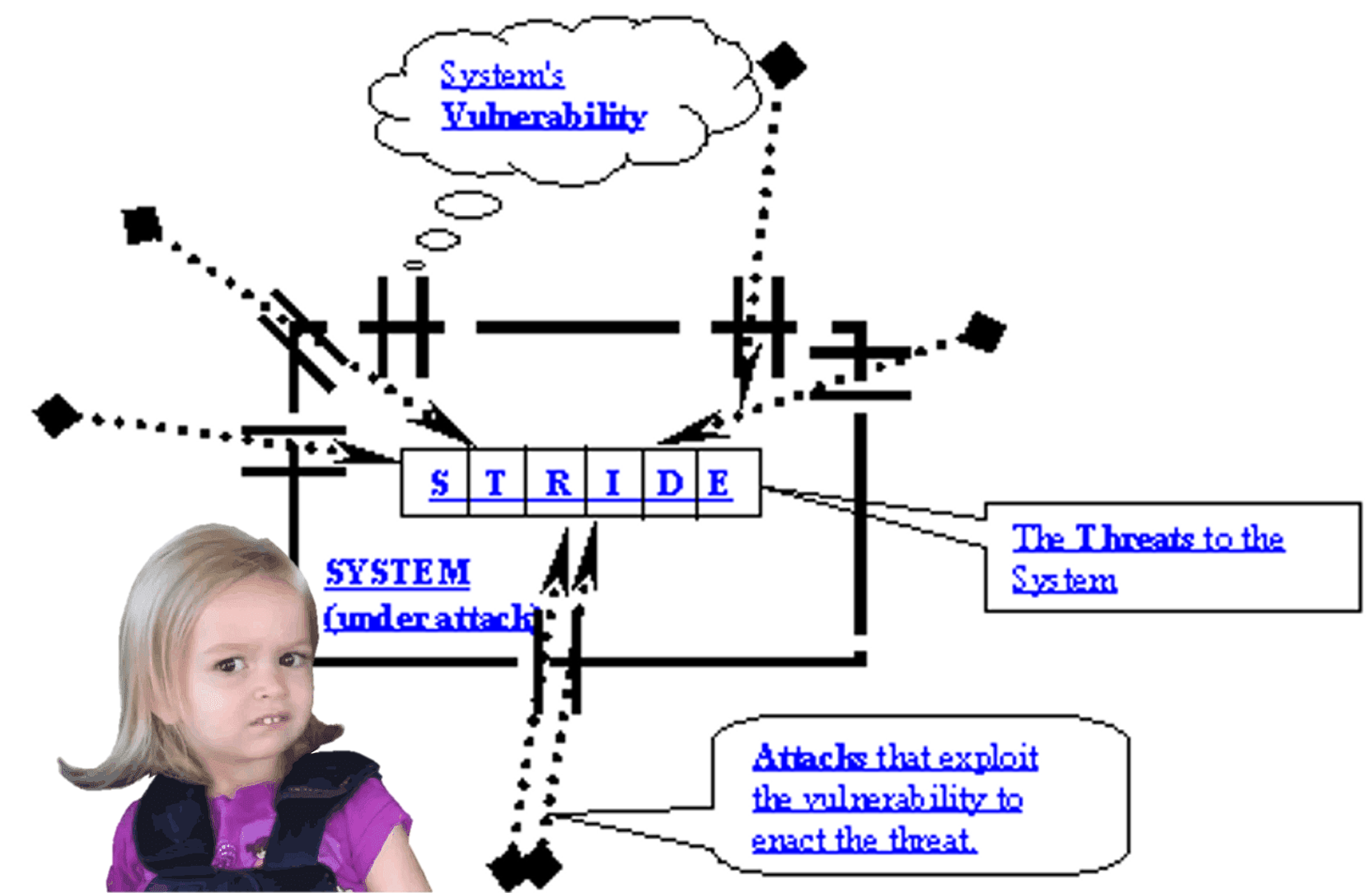
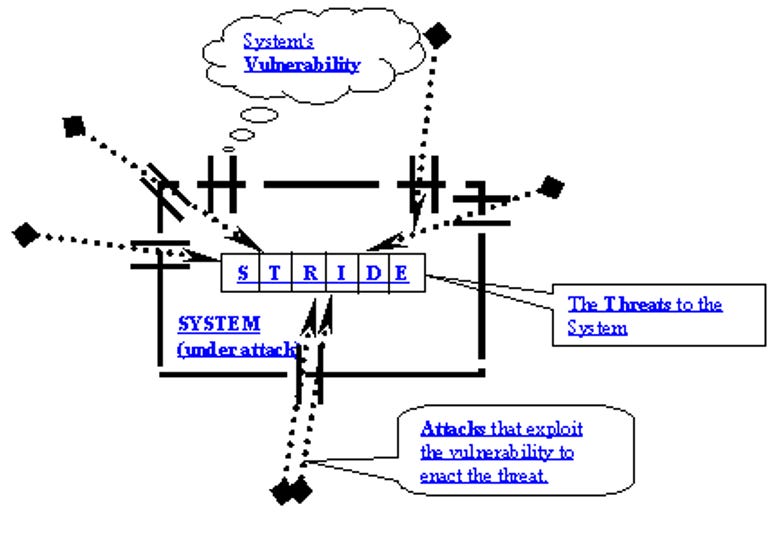
In 1999, the Microsoft Security Task Force introduced the STRIDE “threat” model as a means of identifying threats to Microsoft products during the design phase. STRIDE is an acronym that represents six “threat” categories.

According to the paper that introduced the STRIDE model, “The Threats to our Products”, the intent of these six threat categories is to help identify vulnerabilities and then take measures to close security gaps. This intent is good and there is no doubt that the tool was a net positive for many years as it helped software developers and others consider how attackers exploit vulnerabilities and how to mitigate those vulnerabilities. However, there is a real concern that the terminology used within the STRIDE model has a tendency to create a systemic misunderstanding of the fundamental principles surrounding cyber risk assessment. The definition and use of words like “threat”, “vulnerability”, and “tactic” are important as they serve as a reflection of how cyber risk is understood, assessed, and mitigated.
The STRIDE paper provides the following key definitions:
Threat – Any potential occurrence, malicious or otherwise, that can have an undesirable effect on the system resources (files, registry keys, data-on-wire, etc.). Undesirable effects can be a system crash, the ability to read a sensitive file or modify a registry key, and so forth.
Vulnerability – Some unfortunate characteristic that makes it possible for a threat to occur. Examples include bad security on a file, buffer overflows, and (in a server product running on Windows NT) missing client impersonation calls when servicing client requests.
Attack – An action taken by a malicious intruder to exploit certain vulnerabilities to enact the threat. Examples of attacks include steps taken by a non-administrator to acquire administrator privileges and a technique that allows private data to be leaked.
The definition provided for “threat” is similar to those provided by NIST and others which conflates “threat” with “threat event”. A threat event occurs when a threat agent exploits a vulnerability and the potentiality of it’s occurrence is measured as “likelihood”. The severity of the undesirable effect of the threat event is the impact. These variables that comprise cyber risk is often expressed in the formula below. Here, “threat” is used synonymously with “threat actor”. Even when a threat has no will or consciousness, such as a flood “exploiting” a data center’s vulnerability of being in a low-elevation area of Saint Petersburg Florida, many find it useful and natural to personify threats as agents that takes action to exploit vulnerabilities that cause adverse consequences.

While the STRIDE paper’s definition of threat is appropriately agnostic to whether or not the threat actor or threat agent is malicious or unintentional, “attack” should be understood as a type of threat event that is the result of malicious activity. However, the STRIDE paper defines “attack” as the actions taken by malicious threat actors to exploit vulnerabilities. It would be more accurate to understand these specific actions taken by threat actors to exploit a particular vulnerability as tactics, techniques, and procedures (TTPs). A closer look at the six “threat” categories highlights the inconsistency and confusion surrounding the STRIDE model’s use of the word “threat”.
Is it best to consider spoofing a user’s identity, tampering with data, or privilege escalation as threat events in and of themselves? The desired security property being violated by these three attack techniques, or the vulnerabilities being exploited, is a lack of authenticity, integrity, and authorization, respectively. While STRIDE may assist in identifying a handful of techniques used to exploit weaknesses in a system or program, it is best understood as very rudimentary as it represents a very small fraction of an ever-growing and adapting list of attacker TTPs, as mapped by MITRE’s ATT&CK framework. And what about information disclosure or denial of service? These actions are most closely associated with impact or a final objective / end-goal of some attackers.
One of the best ways to understand the potential confusion, false sense of security, and resulting risk caused by an over-reliance on the STRIDE model is to consider the impact it can have on a cyber risk assessment. What happens when a risk consultant or in-house analyst trying to assess the risk of a U.S. hospital asks their client or management for threat intelligence most relevant to North American medical providers? And in response, thinking the consultant or analyst needs more information about “threats”, they provide this STRIDE table.
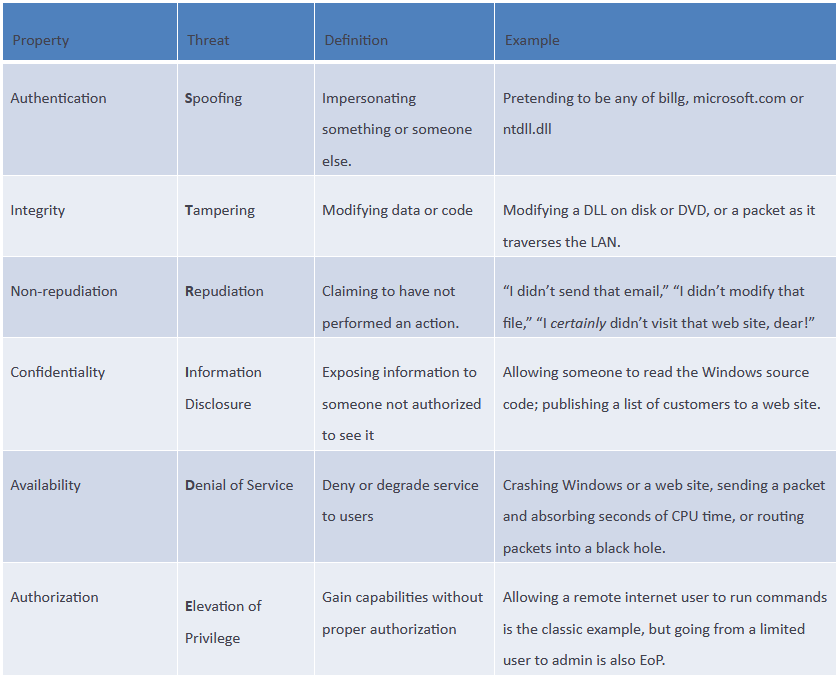
Once a STRIDE-based “threat” analysis has been completed, what will the vulnerability assessment look like? They may mistakenly believe that by looking for evidence of a mere six techniques, they simultaneously assessed both the threats and the vulnerabilities of the network or system. Which part of STRIDE prompted them to consider vulnerabilities relating to the cyber awareness and training of their employees, escort policies, or procurement policies that impact supply chain risk?
Analogies for cyber risk can not only be useful in understanding relevant principles, but it can make the topic much more fun and interesting. The Netflix series Formula 1: Drive to Survive, has helped introduce many Americans to the world’s most beloved motorsport. Let’s consider what a risk assessment might look like for Alpine, a french Formula 1 team. Their threats are best understood as the competing teams, particularly those closest to them in the rankings. Vulnerabilities are things like weaknesses in their car or driver or a budget significantly smaller than their competitors. The consequences of their competitors exploiting their vulnerabilities include not securing a good pole / starting position, losing races and not scoring points, and losing sponsorships.

The STRIDE model in this analogy would be tactics and techniques like slipstreaming and trail breaking. Preventing their competitors from getting an aerodynamic tow and out-breaking their driver are certainly worthwhile considerations for a Formula 1 team seeking to reduce their risk of losing. However, treating a limited set of techniques used by your competitor as the threat itself increases the likelihood of creating competitive blind spots that leads you to fail to consider things like making the son of a Russian oligarch one of your drivers to secure a new sponsor or developing an innovative dual-axis system that improves car performance.
Back in 1999, STRIDE was a forward-thinking tool that helped software developers and IT professionals identify and reduce security concerns. That said, today’s INFOSEC and cyber risk practitioners would be wise to recognize the limitations of the STRIDE model and make sure it does not confuse their understanding of the variables that comprise risk.